
| Project: | TAPAS |
|---|---|
| Internal Release Number: | $Revision: 1.4 $ $State: Exp $ |
| Related Documents: | Software
Requirements Specification |
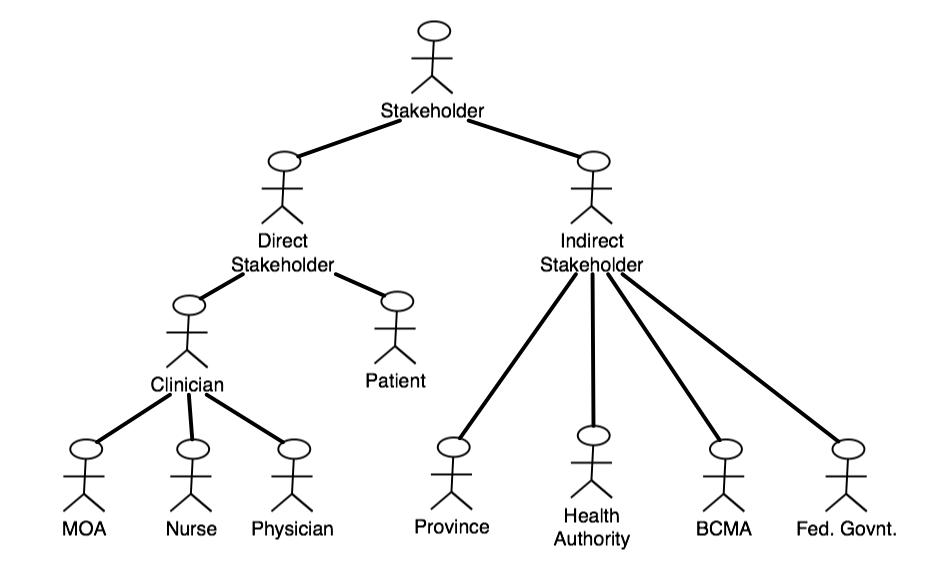
Stakeholders include but are not limited to the actors appearing in the
use case diagram. This is because only direct users of the software system are shown in use case models.
However, from a security point of view additional stakeholders exist,
such as patients, health authorities, and governments. We
distinguish between two main categories of stakeholders, namely direct
stakeholders and indirect stakeholders. Direct stakeholders of
those stakeholders who have some information about them
being exchanged with the system. For these stakeholders we have
to spcify an Information Model that characterizes this
information. This is not necessary for indirect stake holders,
since no information about them is exchanged with the system.
Nevertheless, indirect stakeholders such as governments have important
security goals.
| Kind | Details |
|---|---|
| Structured medical summary documents (e-MS documents) |
Such documents contain details about the patients medical
history, current problems, medications, allergies
etc. A detailed specification of the e-MS document information content was created by the VIHA e-MS group and can be found here. |
| Unstructured messages between physicians that contain data about patients | Similar to electronic mail. These messages may include patient information |
| Kind | Details |
|---|---|
| Audit information about data access |
Clinicians can create, edit, validate, and view patient summaries and demographics. They can also edit on-call schedules. For the purpose of non repudiation, all these information access operations are audited along with the identity of the clinician who perform ed them. |
| User information | Information stored in the system to uniquely identify the user as well as assist in the delievery of care. For example a College ID number would be important as that will be needed both for prescriptions and for referrals. |
| Kind | Details |
|---|---|
| Meta-data in structured medical
summary documents (e-MS
documents) |
e-MS Documents contained
meta-data about the
identities of physicians, their decisions, and their observations. A detailed specification of the e-MS document information content was created by the VIHA e-MS group and can be found here. |
| Unstructured messages between
physicians |
Similar to electronic mail |
| On-call schedules | On-call schedules are Calendar information, which identifies which physician is on call at what times. |
| Local Content | Compressed web pages of content (such as local pharmacy phone numbers) that would be available to the physicains from their PDA. |
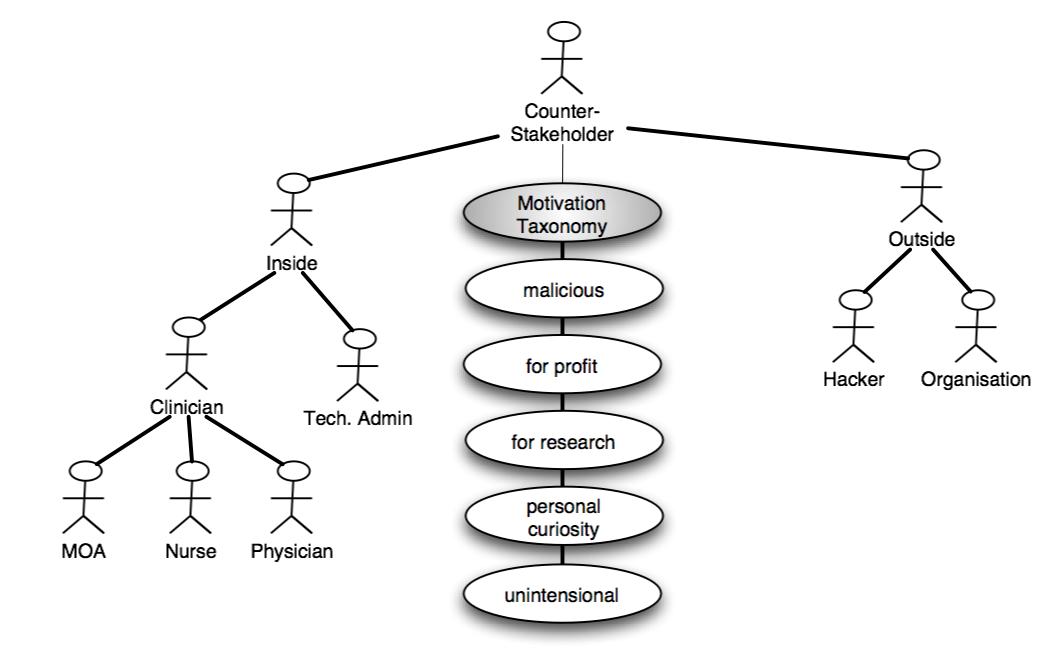
| Counter-stakeholder | motivation | information target | action | resource level (low-medium-high) |
|---|---|---|---|---|
| Outsider | malicious | Patient/clinician information | read (and disseminate), modify, delete | low |
| for profit | Patient/clinician | read | medium | |
| personal curiosity | Patient/clinician | read | medium | |
| Clincian | malicious (e.g., to hide an erroneous diagnosis) | Patient/clinician information | modify, delete | low |
| for profit | Patient/clinician information | read | low | |
| personal curiosity | Patient/clinician information | read | low | |
| unintentional error | Patient/clinician information | read, modify, delete | low | |
| Tech. Admin | malicious, for profit, personal curiosity, unintensional error | Patient/clinician information | read, modify, delete | high |
| Stakeholder | Kind (G/C) | (information) object | quantifier | Counter-stakeholder | Purpose/Episode | Consented/restricted Actions |
|---|---|---|---|---|---|---|
| Patient p | C | structured (e-MS) and unstructured medical information | some | physician c | c treats p | read, modify, delete |
| some | clinician c | c supports physician x x treats p |
read, modify, delete | |||
| G | medical data containing patients
identity |
all | outside Tech Admin |
read, modify, delete | ||
| Physician c | C | e-MS documents created by c for patient p | some | physician x | x treats p c treats p |
read |
| C | messages sent from c to physician x | some | physician x | read | ||
| Provincial Government | G | Identities of patients and clinicians | all | outside | read |