Security Threat Analysis (by computational node)
- 1. TAPAS Server
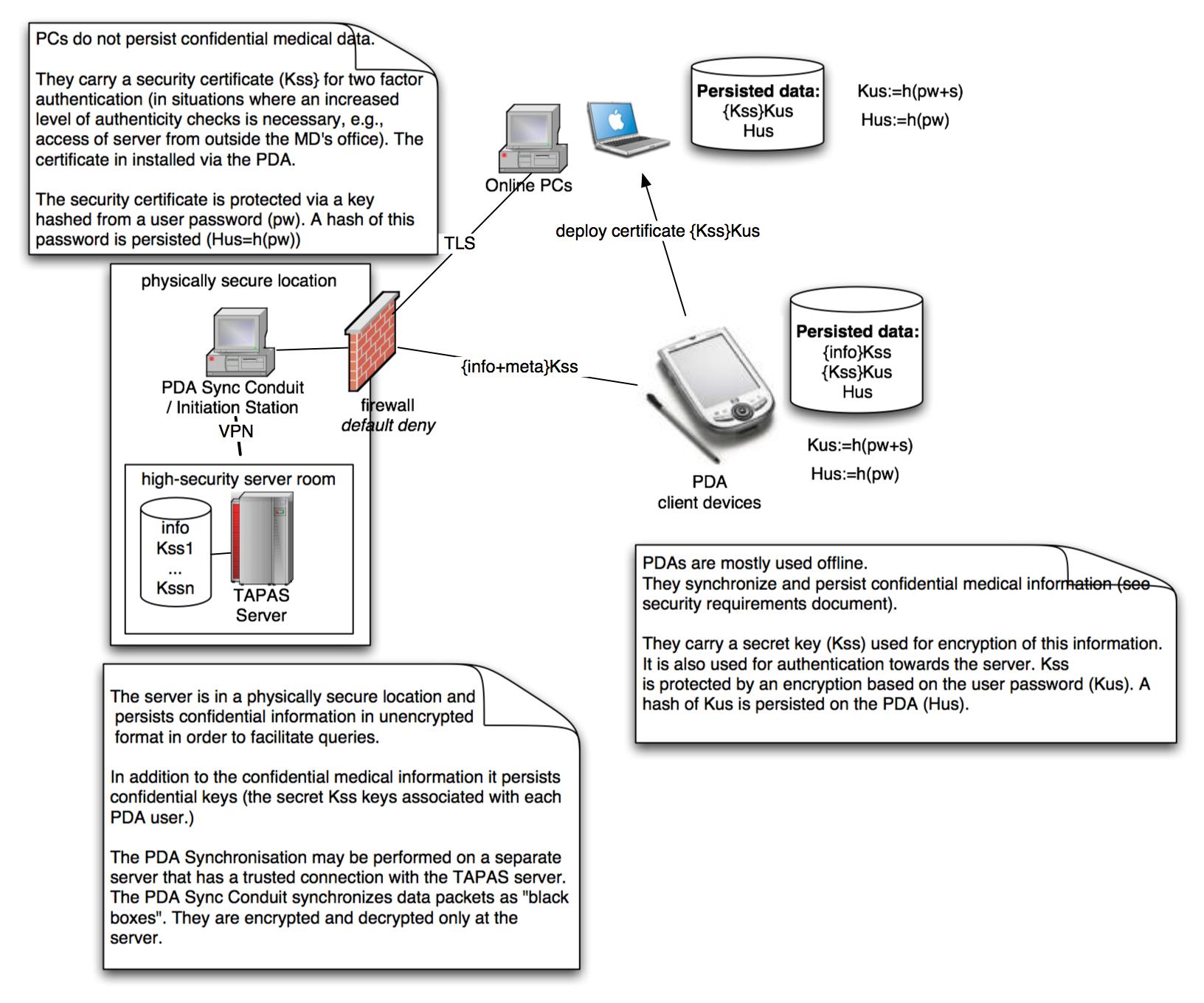
Data: The TAPAS server contains
sensitive data in its database
: private messages,
private encryption keys for
each mobile user, calendar items, and user information. The data is not
encrypted in the server's database.
Threats:
- Data may be accessed/modified by unauthorised users while the
server remains in place
- Server (or parts thereof such has hardrives) may be stolen.
- Data sent or received from the initiation station or the Internet
(through the firewall) may be accessed or modified by intruders
Countermeasures:
-
- Servers will be kept under high physical access security.
(locked room with key available only to administrators)
- Server case itself has a
security cable that prevents the case from being opened (so the
hard-disk with sensitive data cannot be removed).
- Backup tapes are encrypted and stored
in a locked cabinet in a locked room.
- Operation system security:
- Users will not be able to log-in to the server except for
administrators.
- Special "users" will be created for the application (with
minimal permissions)
- Operating system
permissions on files and directories are set to prevent undesired
access or modification.
- Database security:
- DB access control features will be used to control access
to data. Different users will be created for different data sets
(messages, calendar, keys)
- Any access to data on the server is audited
- The TAPAS server will only run software needed for its
operation and any software install has to be approved by an
administrator
- Network security:
- Any sensitive data that leaves the TAPAS server must be
encrypted
- Any host communicating with the TAPAS server must
authenticate with a cryptograhically strong authentication
- Any communication with clients on the Internet is protected
by a firewall that enables only the required ports.
- Sessions are tied to a
particular client IP-address so that stolen cookies cannot be used.
- Sessions time out so
that unattended terminals cannot be abused.
- The data access layer
will allow read-only connections, which will be used for most requests,
as well as write connections for requests that update the database.
- The initiation station's IP and MAC address are registered
(and verified) with the server
- All mobile client MAC addresses are registered (and
verified) with the server
- All Intranet clients (administrative or backup) are
registered with their IP and MAC addresses with the server
- 2. Initiation station / PDA Sync Conduit
Data: The only confidential
data persisted by the initiation station is the private key used to
authenticate the initiation station against the server. Other than
that, the initiation station only deals with information of low
confidentiality, i.e., meta information about messages (sender and
receiver ID, msg number, flags, etc.).
All other information is
encrypted.
Threats:
- An attacker may hack the initiation station and steal the private
key certificate
- An attacker may steal the initiation station hardware or parts
thereof
- An attacker may use the initiation station in-place to initiate
an unauthorised PDA
- An attacker may fake the identity if the initiation station to
get to the server data
- An attacker may fake the identity of the initiation station to
get to authorised user credentials (in order to pose as the user later)
- An attacker may intercept/modify network traffic to/from the
initiation station
Countermeasures:
- The private key will be kept encrypted at the initiation station.
- Password authentication will be used to decrypt the private key
for each initiation action.
- Passwords will be encrypted and checked for quality
- The initiation station will be located in a space inaccessible to
the public (locked office).
- The
initiation station portion will only be activated when new PDAs need to
be added to the system. It will not be active during other times.
- Educational measures:
- TAPAS users will be educated how to confirm that initiation
station users are authentic.
- Initiation station users will be educated how to confirm that
TAPAS users are authentic.
- Operating System security:
- A separate user will be created for the use of the initiation
station software (JSync Manager GUI). OS access rights on the file
system will be set such that no other user can access the JSync Manager
software or data. Likewise, the initiation station user will not be
able to use any other software / data.
- The initation station will be "locked down" such that only
administrators are able to install new software
- Network security
- Any communication with the TAPAS server has to by
cryptographically authenticated (signed by the TAPAS server's private
key)
- Confidential data (message contents, calendar schedules, keys)
will be transmitted to and from the initiation station without the need
to decrypt it.
- 3. TAPAS Synced clients
- Data:
Synced clients are not always
connected to a network. They are mobile, small computers (such as
PDAs). To be useful, they need to persist certain data
provided by the server at the time of synchronisation. This data
includes information about messages relevant to a particular user,
calendar information (call schedules), electronic medical summaries of
patients relevant to this user, and additional confidential credentials
used for authentication and confidentiality (a secret key for encyption). Synchronisation is
performed via the Internet.
Threats:
- Attackers may directly access/modify the confidential data
persisted in the data base of a synced client
- Attackers may access the TAPAS applications on the synced client
in order to get to the data
- The server be faked to gain user credentials (man-in-the-middle
attack)
Countermeasures:
- All confidential data is cryptographically protected on the
synced device. This includes messages (message contents, subject,
addressee and addresser), electronic medical summaries (patient data), and
private
cryptographic keys. (Calendar information is not cryptographically
protected. However, it only contains call schedules.)
- All TAPAS applications require user authentication using a
user-selected password. (This is in addition to the authentication
scheme supported by the PDA operating system. The same password can be
used.)
- TAPAS applications will have an in-activity timeout that will
automatically challenge for re-authentication.
- Synced clients will use strong cryptographic authentication
whenever they sync up to the server. The authentication will be based
on a secret key installed at the time of device initiation. This secret
key will be persisted in encrypted format on the synced client (using
the user's password). The key will be unique per device and therefore per
user as each user is given a specific PDA on their account.
- In addition to the secret authentication key, the tapas server
will check the clients serial number and network adapter (MAC) address.
- The secret key will also be used to authenticate the server to
the client (and prevent man-in-the-middle attacks).
- 4. TAPAS Online clients
Data: While confidential data
should not be stored on the client online machines, Web browsers have a
cache that may automatically store confidential data. Session cookies
may be persisted as well. Moreover, we cannot technically prevent the
user from downloading and saving confidential data to their local
machines. In contrast to TAPAS synced clients, online clients are
permanently connected to the network. They do not need to persist
medical summaries, calendars, messages etc. The only confidential data
persisted on PCs running online clients are cryptographic key
material used for authentication.
Threats:
- Attackers may directly access/modify the cryptographic key
material
persisted at the online client
- Attackers may access the TAPAS applications on the online client
in order to get to the data
- The server be faked to gain user credentials (man-in-the-middle
attack)
Countermeasures:
- Online clients use the same strong cryptographic authentication
that synced clients use. The initiation of an online client is
performed with an initiated synced client.
- All TAPAS applications require user authentication using a
user-selected password.
- TAPAS applications will have an in-activity timeout that will
automatically challenge for re-authentication.
- The secret key will also be used to authenticate the server to
the client (and prevent man-in-the-middle attacks).
- In addition to the secret authentication key, the tapas server
will
check the ip address and the network adapter (MAC) address of the
online client.